MFA, EDR, and PAM, oh my! Despite having more tools and controls than ever, we still have breaches. What's really happening?
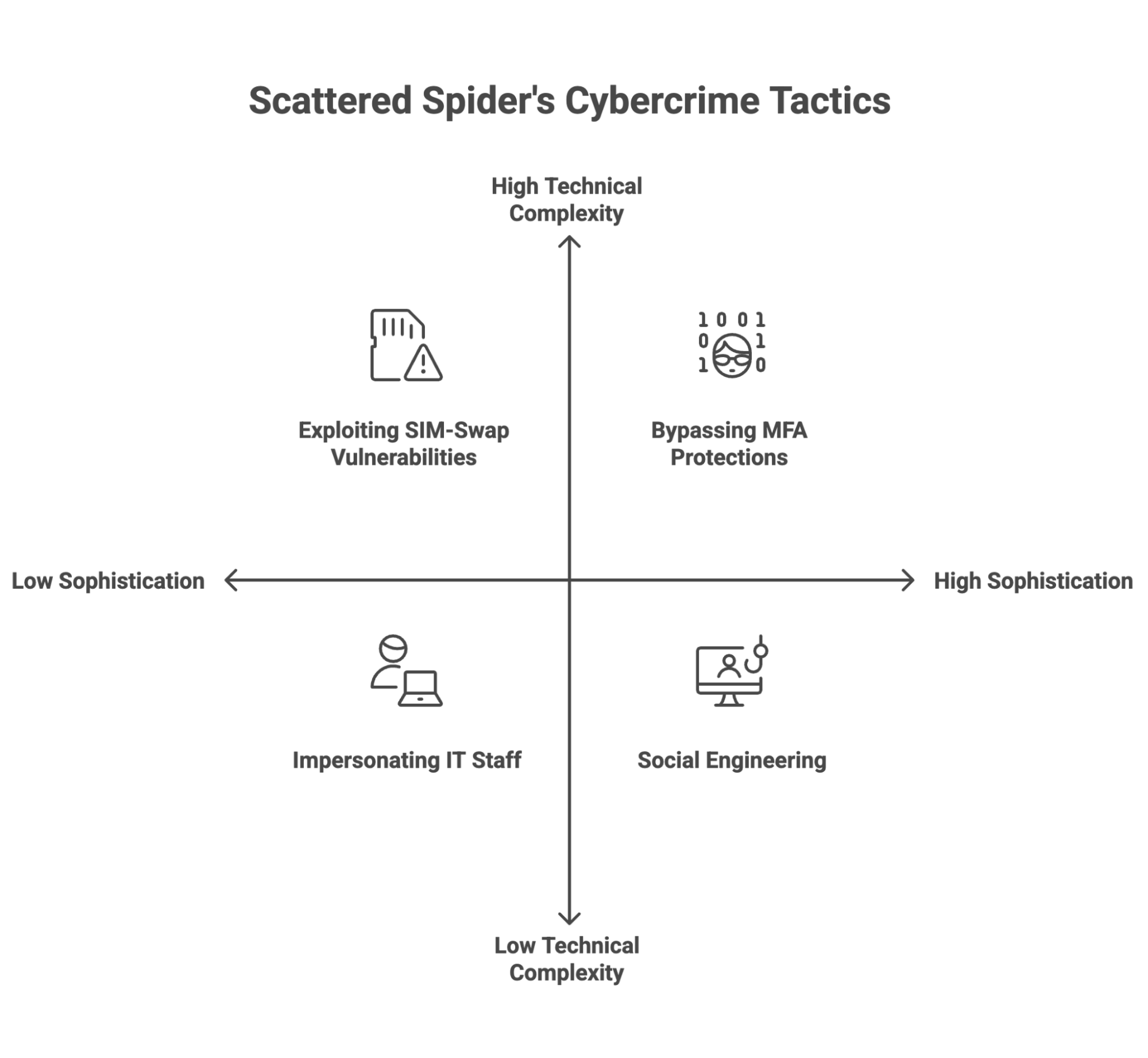
Scattered Spider is rewriting the cybercrime playbook. This group doesn't depend on malware or brute-force attacks; they exploit trust.

Unfortunately, Cozy Bear is one of the most innovative and creative APT groups out there. Instead of just adding more tools, let's see how they bypass the ones we have and how to counter them.

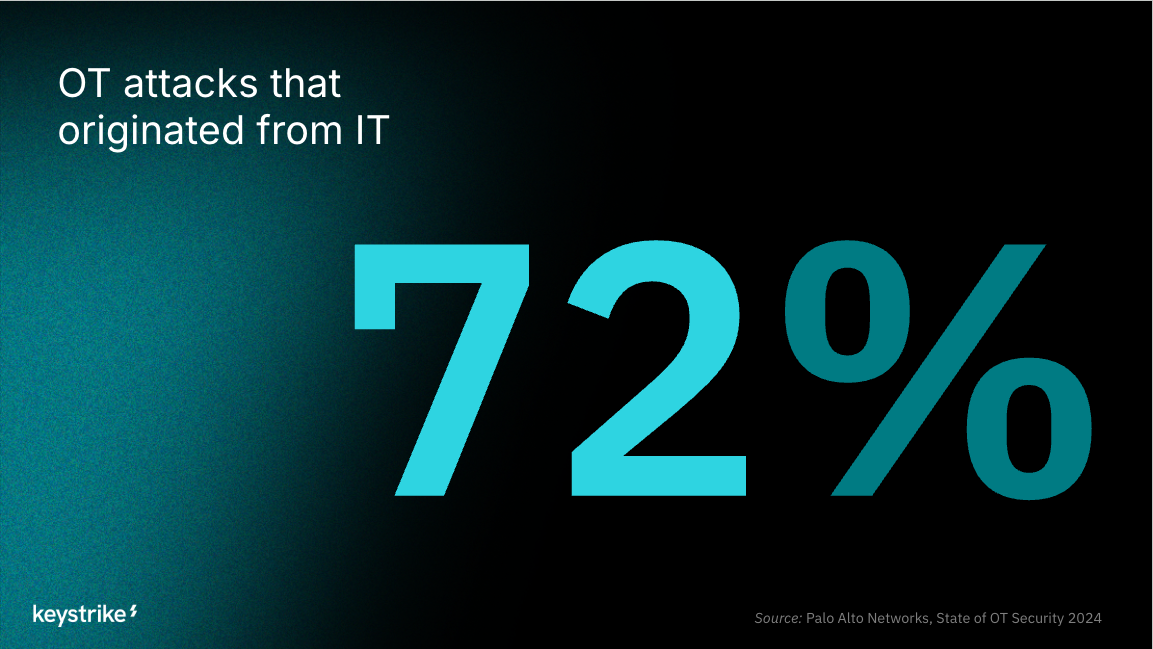
While we've hardened our perimeters and identity controls, our workstations are still great targets for motivated attackers.

While CISA has warned us about Iranian cyber threats, the events of this weekend put it in the forefront everyone's mind. Dive in to find out how to protect yourself.

Throughout our deep dives into the various Typhoon APT groups, we saw that our existing controls still aren't enough. Instead of adding more defenses on the perimeter, let's think about some depth.

All of our security tools, practices, and controls are based on a series of assumptions. What if those assumptions are wrong? Do our tools still protect our systems?

Volt Typhoon has quietly moved through critical infrastructure networks, unseen and unchallenged. Unlike gangs that try for disruptions, Volt Typhoon takes a stealth-first approach.

Attackers quietly living off the land is one of the most devastating threats to our systems. How do attackers manage it without detection?

The adversaries targeting water infrastructure are skilled, organized, and often well-funded. Understanding how they attack is as important as why they attack.

For years,Chinese state-sponsored attackers have moved through networks of the most critical industries—telecommunications, energy,defense, and government. Not to vandalize,not to ransom,but to wait.
Try Keystrike in your environment for free for 30 days
