
Ymir Vigfusson
August 19, 2025

Cozy Bear, also known as APT29 or Midnight Blizzard, sets the benchmark for advanced persistent threats. Regarded as trailblazers among threat actors, they consistently pioneer sophisticated techniques that other groups inevitably follow. Their operations represent the leading edge of cyber espionage, not out of admiration, but acknowledgment that understanding their methods today prepares you for tomorrow’s threats.
Understood to be operating under Russia’s Foreign Intelligence Service (SVR), Russia's equivalent to the CIA, the Cozy Bear group has executed long-term, high-value intrusions across both public and private sector targets, including the SolarWinds attack. That attack is arguably the most infamous software supply-chain breach ever affecting prestigious entities such as the U.S. Department of Homeland Security, the Department of the Treasury, Microsoft, and other leading Fortune 500 organizations. To anticipate the next wave of APT innovation, we need to look closely at what Cozy Bear is doing now.
Unlike financially motivated adversaries, Cozy Bear doesn't rely on malware to infect their hosts after smashing through defenses. Instead, they operate with surgical precision, compromising supply chains, abusing identity infrastructure, and turning authenticated user sessions into covert command channels.
Their greatest strength lies in how they manipulate trust at every layer: the workstation, the session, and the cloud services your SaaS applications depend on, highlighting the critical need for solutions like cloud protectors that secure these increasingly exploited interfaces.
Your Workstation; The Attacker’s Proxy
Once an attacker compromises a single endpoint, your workstation transforms from a mere access point into a proxy for the adversary. Every seemingly legitimate command, credential replay, or interaction with the APIs powering your SaaS applications can now originate directly from your compromised workstation, turning your trust boundary against you. The attacker doesn’t have to break every lock; they only need to speak through your workstation’s voice.
Let’s dive into the Cozy Bear tactical progression to see why traditional detection fails, and how a fundamentally different approach, rooted in input-level verification, neutralizes the attacker’s advantage.
Like most APTs, Cozy Bear started with custom malware. But what makes them elite is how quickly they adapt. Over the last decade, they evolved from dropping binaries to hijacking your infrastructure.
Here’s a snapshot of their tactical shift:
Instead of looking like malware, Cozy Bear started looking like your systems administrator. They invoke legitimate tools already present on the machine, because these LOTL techniques are significantly harder to detect. Once a zero-day exploit is discovered, security tools rapidly update their detection. In contrast, abusing legitimate protocols like RDP and SSH can continue indefinitely; these aren't exploits; they're the protocols functioning exactly as intended. The real exploit lies in compromised accounts and session abuse.
For example, attackers commonly use native tools to harvest credentials and tokens silently, bypassing endpoint detection. A typical scenario involves credential dumping via a legitimate PowerShell command:
PowerShell
Invoke-Command -ScriptBlock {
rundll32.exe comsvcs.dll, MiniDump (Get-Process lsass).Id lsass.dmp
}Attackers extract these credentials and tokens to impersonate legitimate users, enabling access to sensitive targets without alerting EDR solutions.
There’s no implant, no executable. Just a native tool. And because these actions often occur inside a legitimate RDP or SSH session, most EDRs never raise an alert.
Then they moved to the cloud.
Once they compromise a user’s token, they access APIs across cloud platforms like Microsoft 365 and Google Workspace. Here’s what it looks like when they replay a stolen OAuth token:
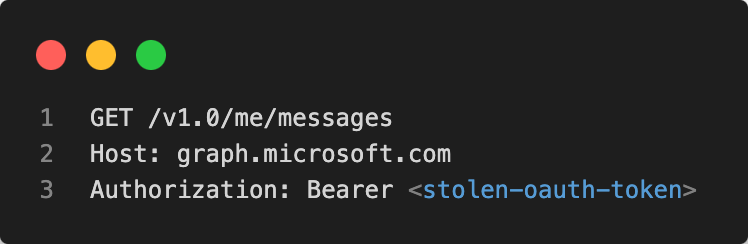
No malware, no new executables, just an authenticated API call.
The hard part about finding Cozy Bear isn't the strange exploits; it's that Cozy Bear can act like a real user. Session hijacking, credential replay, and token abuse are all used to create seemingly typical activity. As a result, defenders who rely solely on pre-authentication security controls can’t detect actual breach activity.
Let’s look at their stealth tactics more closely:
Attackers authenticate using stolen credentials and act like insiders, which eliminates the need to guess passwords or scan ports.
Here’s how that session misuse looks in practice:
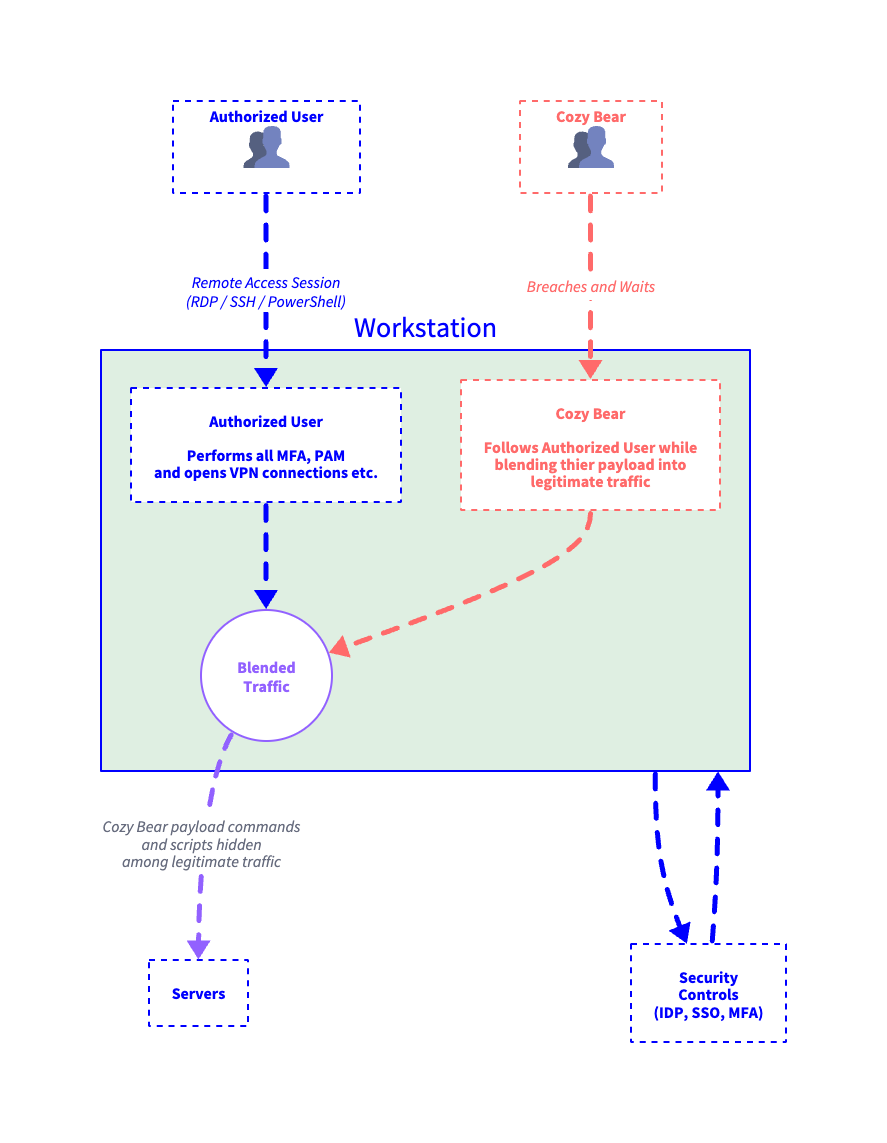
Because they're exploiting an authenticated session, traditional security tools trust the traffic. Your workstation effectively becomes a zombie, silently facilitating Workstation-as-a-Proxy (WaaP) attacks by forwarding attacker commands and exfiltrating sensitive data undetected.
SolarWinds: The Ultimate Stealth Campaign
The SolarWinds breach represented a strategic escalation. By compromising a reliable update pipeline, Cozy Bear gained systematic access to thousands of downstream systems.
Cozy Bear injected malware into Orion, SolarWinds’ software update platform. The code passed all build checks, got signed, and shipped to 18,000 customers, including U.S. federal agencies and major corporations, such as the Department of Homeland Security, Department of State, National Institutes of Health, and leading global corporations.
Here’s a quick view of the compromise chain:
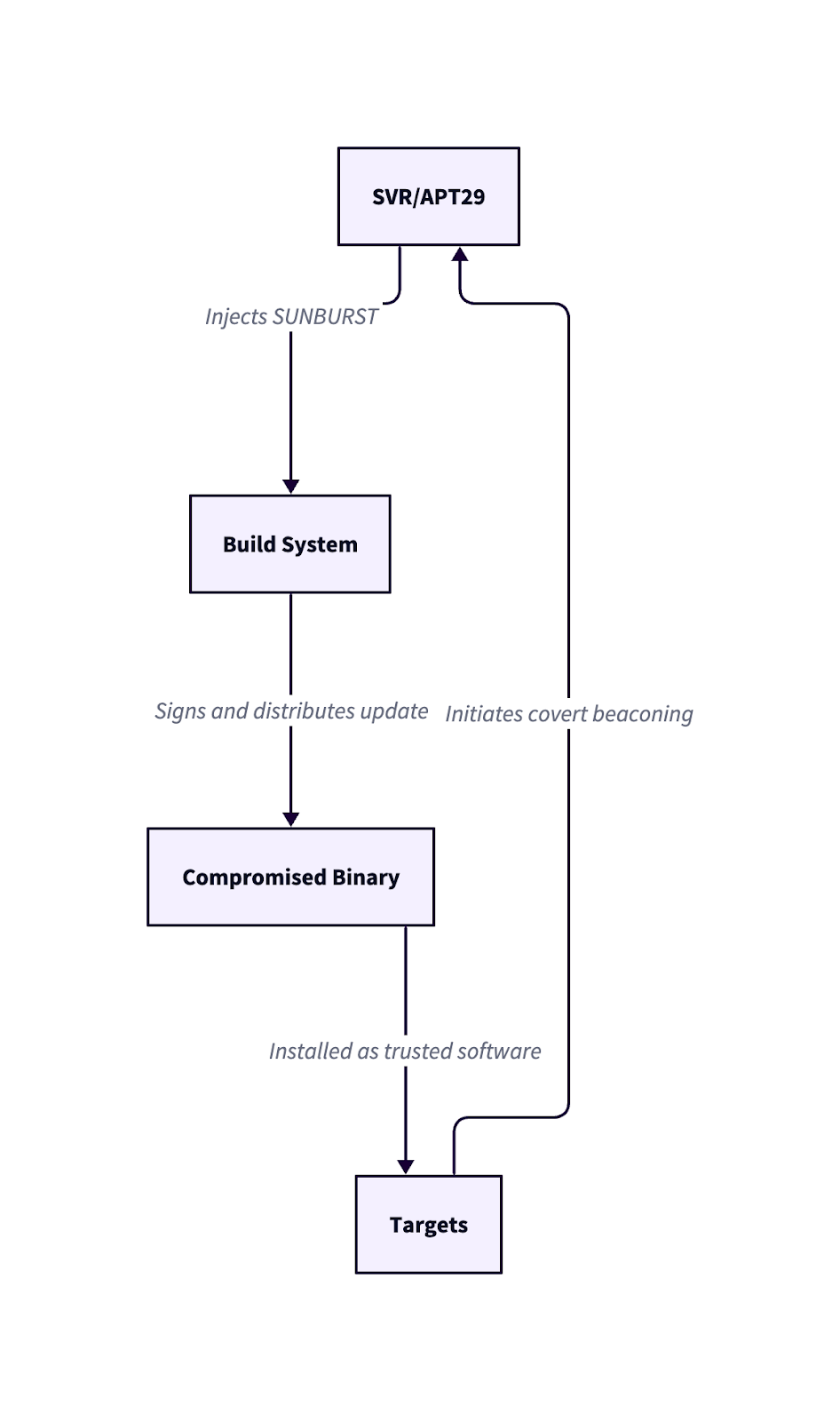
After gaining access, Cozy Bear escalated using SAML token forgery and executed commands via native tools, exfiltrating data silently.
Most tools we rely on, EDR, NDR, SIEM, and SOAR, focus on detection before or during authentication. Cozy Bear exploits the blind spots and gaps after that because of the temporal nature of session authentication.
SSH and RDP sessions lack monitoring capable of differentiating attacker-driven actions from legitimate user behavior. In WaaP attacks, security tools inherently trust the session after successful authentication, providing full operational trust to the attacker.
User and Entity Behavior Analytics (UEBA) tools can flag anomalies, but often only after damage occurs. They don't validate who is typing and they still operate under the assumption that the session is legitimate.
Here’s how a hijacked session bypasses controls:
If Cozy Bear thrives on trust of sessions, credentials, and automation, Keystrike breaks that cycle at the root. Cozy Bear’s entire strategy hinges on one critical assumption: once they insert themselves into your authenticated sessions and leverage your legitimate tokens, they can impersonate you to stay hidden.
Keystrike makes that assumption obsolete.
Instead of trusting sessions based on authentication alone, Keystrike enforces trust at the input level. Every keystroke, command, or click must originate from a verified human on a cryptographically verified input device. No physical presence, no command execution.
By verifying input at the hardware level, you can block automation, token replay, and session hijack, even inside trusted connections. This breaks you out of the Workstation-as-a-Proxy model in a way that traditional tools can’t
Let’s map Cozy Bear’s abuse path against how Keystrike shuts it down:
This is not about more visibility or smarter AI; it’s about eliminating the attack surface entirely by removing input automation from the equation.
If Cozy Bear can’t fake the presence of a human at the keyboard, they can’t operate at all.
The attacker isn’t knocking at the door anymore; they’re already inside the session, inside the cloud, inside your trust boundary. Cozy Bear operates using your permissions, your credentials, and your tools. They quietly use your workstation as a proxy while your software and tools assume that every authenticated session equals legitimacy.
That assumption is where we lose. The only way to win is to demand proof of presence. Not at the perimeter, but inside the session, at the moment of input.
Keystrike gives you that control. It verifies that every action on a system was physically performed by a human, using a real device. No session hijack. No token replay. No silent automation. You don’t just lock Cozy Bear out, you erase the path they rely on.
If your goal is to eliminate session-based stealth from your threat model, Keystrike is built for that fight. Schedule a demo with Keystrike to see input-level trust in action. Stop assuming. Start verifying.
Try Keystrike in your environment for free for 30 days
