
Keith Casey
October 14, 2025
Critical infrastructure operators have made big investments in strong perimeter defenses. Everything, including multi-factor authentication (MFA), endpoint detection and response (EDR), and privileged access management (PAM). Yet breaches still regularly occur, mostly unnoticed until it’s too late. The problem is that these tools are designed with a specific purpose and specific assumptions, but they don’t address the way modern attackers operate.
State-aligned APTs and organized ransomware operators often begin by compromising a legitimate user’s workstation. Once they establish this foothold, every move they make appears to originate from a trusted device, over an authenticated VPN session, using valid credentials. From the network’s perspective, the activity satisfies every security check and blends seamlessly with legitimate traffic.
This is why campaigns like Russia’s Sandworm attacks on European energy operators or China’s Volt Typhoon operations against U.S. facilities trigger no alerts. An operator logs in normally, but the compromised workstation soon issues remote commands to critical servers. To existing defenses, it still looks like the same authorized user working within a trusted network, even though the attacker is now in control.

The underlying weakness is that defenses validate identity at a moment in time but rarely check whether the person still controlling the session and sending commands is the original, legitimate user. Once attackers have the session, they can move without resistance. This is why trusted session misuse is at the core of so many breach playbooks.
Modern attackers don’t waste time on noisy exploits when they can start with keys that already work. Valid credentials or hijacked sessions give them the fastest route to stealth and persistence.
Attackers gather credentials through targeted phishing, credential stuffing, and direct exploitation of public-facing services. Phishing remains the most reliable approach, using cloned login portals or malicious attachments to harvest usernames and passwords. MFA bypass is common, using MFA fatigue or social engineering against help desk teams to get reset links or one-time codes. This is especially troubling when the credentials belong to someone with administrative privileges.

Credential reuse is another high-return tactic. Password dumps from unrelated breaches feed automated login attempts against corporate VPNs, RDP gateways, and cloud management portals. Weak password rotation policies amplify the success rate.
Public-facing services give attackers a direct network path. Misconfigured or unpatched RDP gateways, VPNs, or application portals can provide immediate internal access. Volt Typhoon has repeatedly leveraged stolen accounts to connect via legitimate RDP infrastructure, often reusing a session that already passed MFA earlier that day.
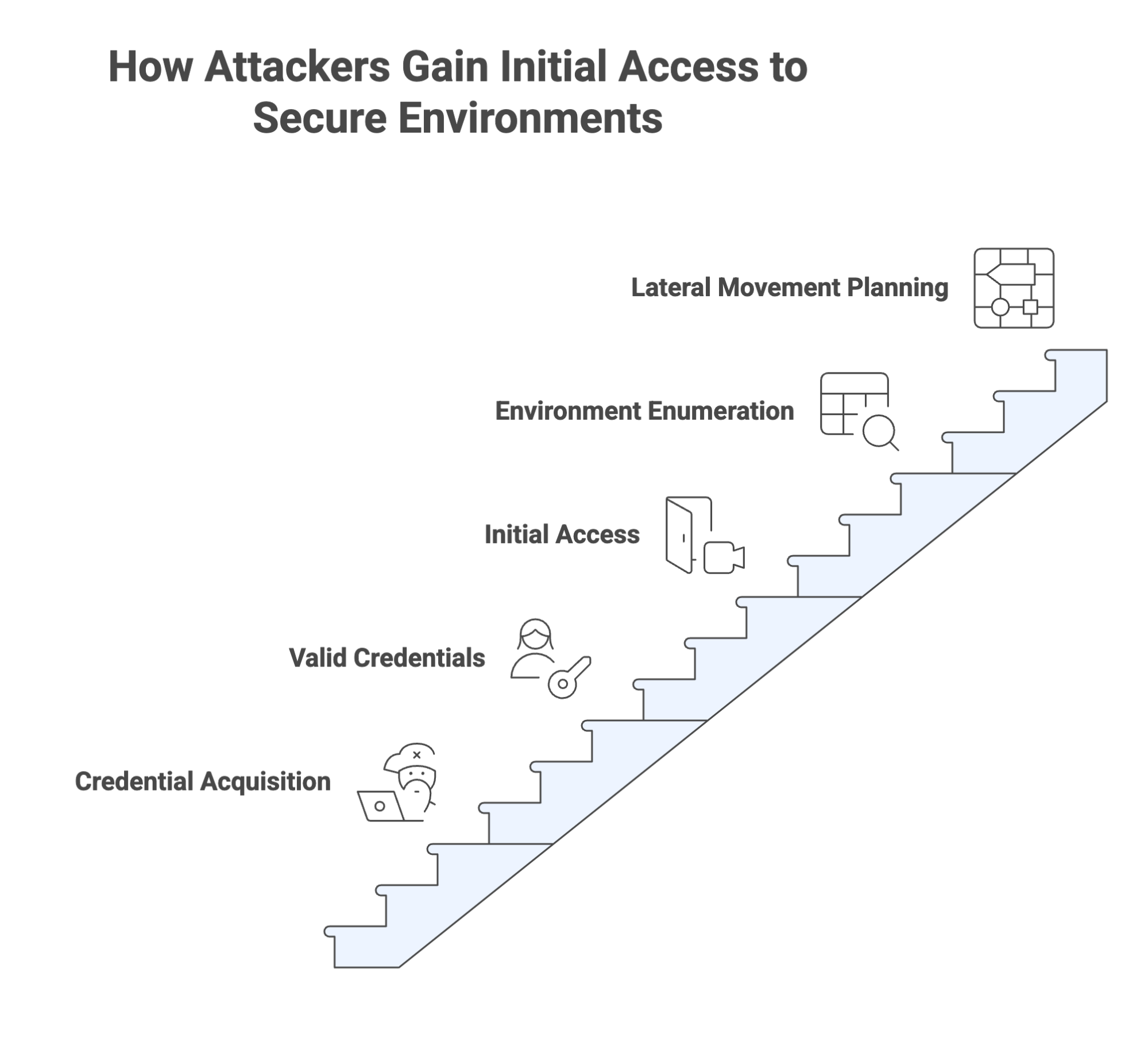
Once inside, the attacker rarely launches malware immediately. Instead, they analyze the environment, identify administrative tools in use, and plan how to move laterally without raising suspicion.
The most damaging phase of any breach happens after initial access. Lateral movement lets attackers expand from a single foothold to the systems that matter most: domain controllers, file servers, database clusters, and industrial control systems.
MITRE and CISA data show that over 70% of observed breaches use remote services for lateral movement. The techniques are few but effective:
These tools are part of daily operations for administrators. That makes them excellent cover for attacker movement. No exploit is required; the attacker simply uses existing administrative protocols over an already trusted session.
Security teams often over-focus on preventing the initial “land” phase of compromise. While this is critical, users make mistakes. They click on a bad link, run a command from an “admin” on the phone, or enable that macro. Teams have to be successful every time, while an attacker only needs one success.
The “expand” phase, where attackers move toward high-value assets, is under-monitored and under-protected. When attackers start expanding, their activity appears to be the same as legitimate IT work. By the time defenders detect anomalies, attackers may have already accessed sensitive data or carried out destructive actions.
This failure is due to a fundamental architectural flaw. The assumption that once a session is authenticated, it remains trustworthy throughout its entire duration.
Multi-factor authentication, privileged access management, and endpoint detection all have a blind spot: they trust the session once it’s established. When an attacker compromises an endpoint, they inherit everything on it, including:
With these in hand, they can move across the network without re-authenticating.
Attackers execute commands through built-in administrative tools. EDR sees only legitimate binaries in use. PAM sees an authorized account operating within its allowed window. MFA never re-triggers because the second factor was completed earlier. Every action looks legitimate in isolation, but the real user isn’t the one issuing the commands.

For example, an attacker uses cached RDP credentials to log into a database server, runs a PowerShell script to export data, and then closes the session. All activity appears normal from an authentication standpoint. Without verifying that each command originated from actual user input, defenders cannot separate malicious remote administration from legitimate work.
Attackers can phish credentials, bypass MFA, and hijack active sessions. They can replay commands, deploy scripts, and move across the network, all while looking identical to an authorized administrator. What they cannot do is produce real-time, human physical input from the legitimate user’s workstation during that hijacked session.

If a remote command executes without a matching keystroke or mouse event from the authenticated user, it isn’t legitimate activity; it’s an attacker operating inside a trusted session. Physical input validation makes that difference visible in real time.
The table below shows how the trust model changes when physical input becomes part of the verification process. Trust is no longer tied only to who authenticated at login, but to whether the same user is still present when the command runs.
Post-access, attackers rely on lateral movement through trusted sessions because those sessions bypass most detection methods. Keystrike breaks that chain by requiring proof of live user activity for every privileged remote action. If no physical input is present, the command never reaches the target system.
This is not anomaly detection, heuristic scoring, or behavioral guesswork. It’s a binary control: either the real user triggered the command, or they didn’t. In a hijacked session, that answer is always “no,” and Keystrike turns that into an immediate block, shutting down the attacker’s most reliable tactic before it touches critical infrastructure.
Most modern breaches succeed because attackers operate inside trusted sessions. Traditional controls see those sessions as valid and grant them the same access as the legitimate user for the lifetime of the session. That trust is misplaced.
The fix isn’t more authentication challenges or heavier logging. The fix is to confirm, in real time, that the user at the endpoint is the one issuing the commands. This is Keystrike’s approach: binding remote command execution to verified physical input so attackers cannot ride along invisibly.
By stopping lateral movement at the root, before it can touch critical systems, defenders can turn the attacker’s most reliable tactic into a dead end.
Try Keystrike in your environment for free for 30 days
