
SIEMs are a great tool for investigation after an event occurred but what if we could use them to prevent the event in the first place?
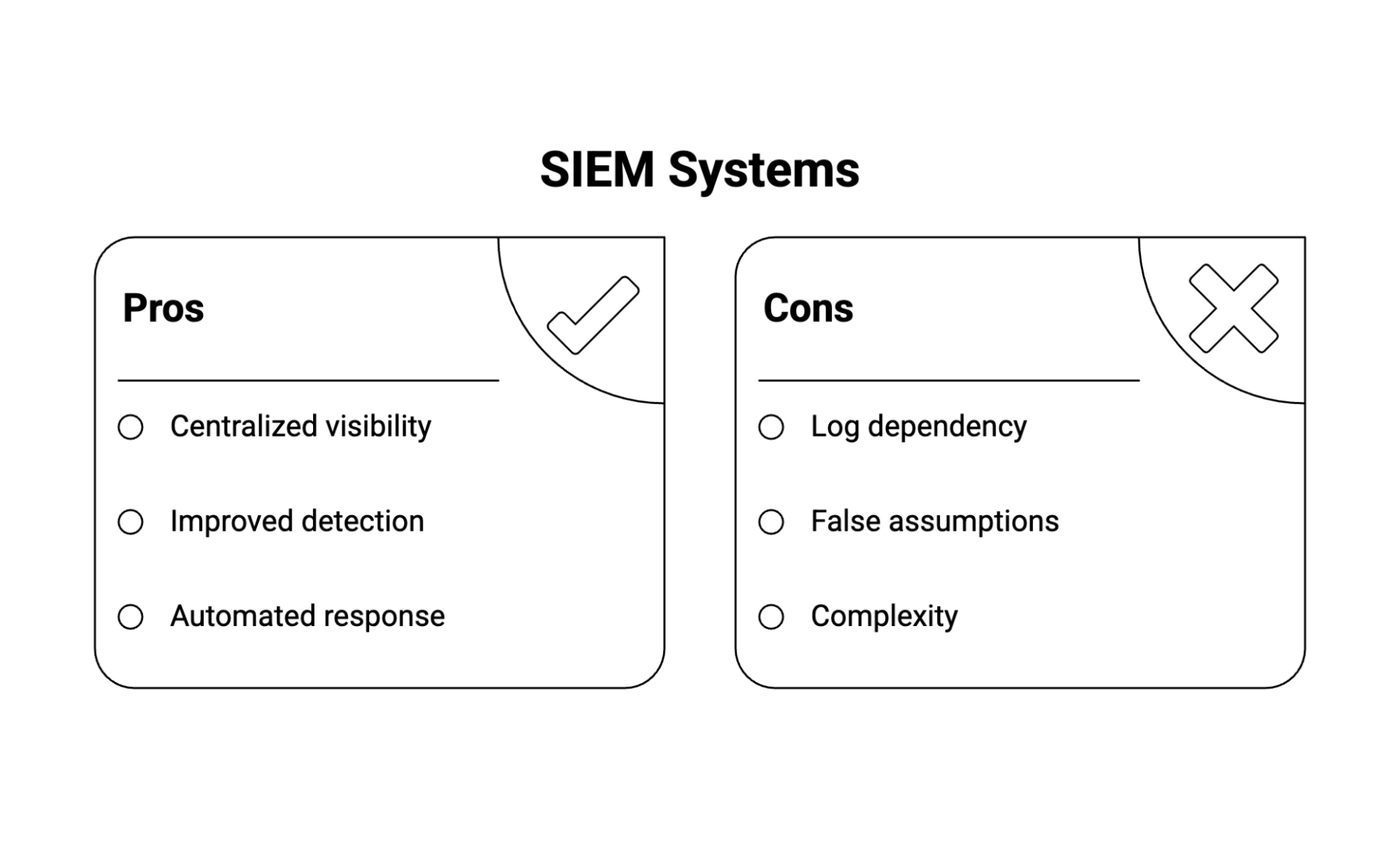
SIEMs are a critical part of our security infrastructure but between false positives and response time, they're not nearly enough. How can we change that?

The danger to your infrastructure isn't in your protocols. Every protocol - yes, even Telnet - has legitimate use cases but you need to consider how to protect them.
Try Keystrike in your environment for free for 30 days
