
Keith Casey
September 30, 2025
For two decades, Security Information and Event Management (SIEM) has been a central component of enterprise cybersecurity defense. SIEM tools collect logs, correlate events, and provide security analysts with aggregated alerts that they depend on for forensic analysis. Most CISOs and Security Operations Center (SOC) leaders cannot imagine defending their environments without it.
However, there’s a fundamental problem: SIEM relies on the information provided by the logs. SIEM tooling depends on the validity and accuracy of its inputs. This becomes a pervasive problem with session trust. SIEM assumes that if a session begins valid, then activities within it are also legitimate unless proven suspicious. Attackers exploit this assumption. They hijack trusted sessions, blend their own commands that seem normal, and allow SIEM to record everything as if nothing is amiss.
While logs can indicate what occurred, they cannot identify who actually entered the command. This blind spot leaves SOC teams vulnerable, even when their SIEM is functioning at full capacity. To better understand the issue, let’s explore how SIEM operates and where attackers manage to evade detection.
To understand the risks and shortcomings in current security practices, it's helpful to take a step back and examine the evolution of SIEM systems. What started as a simple method for centralizing logs has evolved into a core component of security operations. This highlights both the strengths of SIEM and the limitations that attackers can exploit.
The first generation of SIEM solved a visibility problem. Enterprises had logs scattered across servers, endpoints, and firewalls. By pulling everything into one place, SIEM gave security analysts a chance to correlate information that could indicate attacks they might be blind to.
Over the years, SIEM has become a central system of the SOC. Modern platforms ingest logs from on-premises systems, cloud platforms, application logs, network streams, and identity providers. They run correlation rules, flag anomalies, and send alerts when activity crosses a threshold.
To improve detection, vendors added machine learning, anomaly detection, and User Behavior Analytics (UBAs). Later, SIEM connected with Security Orchestration, Automation, and Response (SOAR) platforms to automate playbooks and reduce response time.

Despite all this positive progress, the foundation never changed. SIEM is still only as strong as the quality of the signal it can gather from logs and alerts. If those logs represent hijacked sessions, then the SOC is working from tainted data from the start.
This blind spot is not about missing data. SIEM collects plenty of information. The problem lies in what the data can and cannot reveal. SIEM is logging activities, but not intent. To see why, we need to look closer at the limits of logs themselves.
Logs are excellent at recording events: a PowerShell command executed, a remote session opened, a file accessed. But logs cannot capture intent. They cannot tell if a trusted administrator actually typed a command or if an attacker sent the command in a stolen session.
For example, an intruder steals RDP credentials and connects to the environment. He starts running PowerShell commands to map the network and search for new targets. From the SIEM’s perspective, it all looks normal. A valid account is active. Commands are being executed that an admin might run on any given day. The system has no way to show that the person behind the keyboard is an attacker.
This blind spot exists because SIEM assumes that once authentication succeeds, everything else in the session must be legitimate. But sessions last hours or even days. Control of them can change hands long after login. Logs record the activity, but never prove its origin.
There’s an inherent risk in the routine nature of log aggregation: it’s only valuable to use AFTER the attack. This is why attackers intentionally exploit that perception. Understanding their tactics clarifies why SIEM struggles to distinguish between malicious use and legitimate administration.
This gap becomes most dangerous when attackers start moving laterally. Groups like Volt Typhoon and Scattered Spider thrive by abusing built-in tools. Their operations rely on techniques that are almost indistinguishable from normal administrative work.
Attackers often use PowerShell remoting, PsExec, and WMI execution. Each is a legitimate method for managing systems in large environments. The SIEM sees the commands and records them, but has no way to know they were launched by an intruder rather than a sysadmin.
SOC teams face thousands of similar events every day. They cannot investigate them all, so they lean on thresholds and baselines. Attackers understand this and stay within those patterns. The result is that they move across the environment in full view of SIEM, while the system dutifully logs every action as routine.
Security teams are under significant pressure as modern SIEM systems handle millions of events each day. Despite using correlation and filtering, the sheer volume of alerts that land in the SOC is overwhelming. Many of these alerts turn out to be duplicates, false positives, or low-value signals.
An ESG study cited by Microsoft found that 44 percent of SIEM alerts go completely uninvestigated. This isn't due to a lack of effort; it's a matter of capacity. Human teams simply cannot manage the volume of alerts, and the tools at their disposal often lack the necessary context to identify which alerts represent genuine threats.
Alert fatigue sets in, and security analysts become desensitized to the constant stream of notifications. This can lead to alert blindness, flattened morale, increased burnout, and even staff turnover. Meanwhile, stealthy attackers continue to generate seemingly “normal” events, which slip through the cracks unnoticed.
The combination of excessive noise and blind spots allows lateral movement to succeed, even when the SOC is diligently performing its duties.
Logs give visibility, but only after the fact. By the time SOC analysts review a suspicious entry, the attacker may have already escalated privileges or deployed ransomware. Detection becomes an exercise in forensics rather than prevention.
More importantly, logs cannot prove the input source. They show that a command ran, but not whether it was issued by:
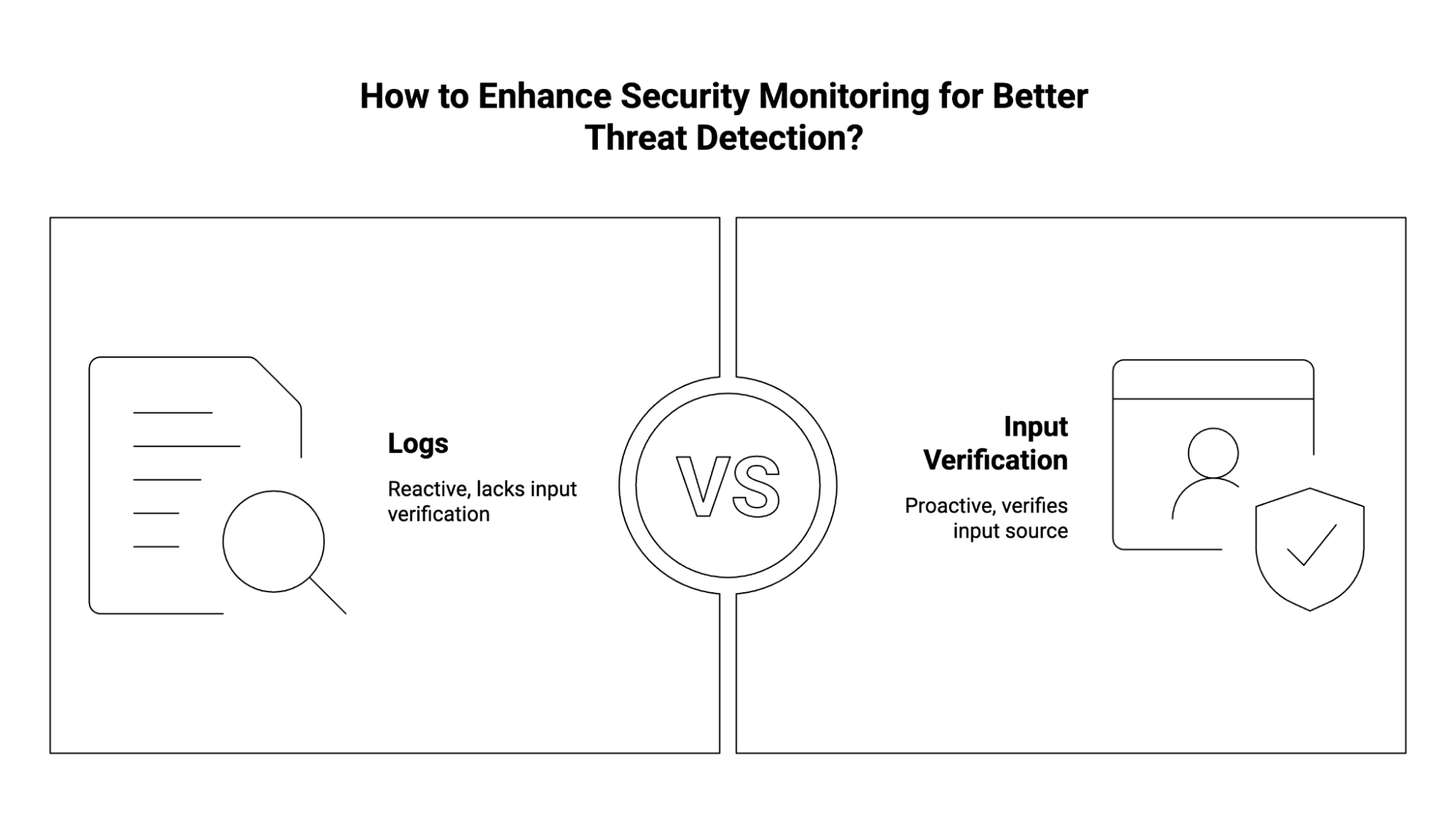
This is why modern attacks slip through SIEM undetected. The logs look fine, but they are built on compromised sessions. Without verifying input or intent, SOC teams are left guessing whether the data in front of them reflects trusted activity or adversarial control.
Solving this problem requires a new signal: proof that every command came from a legitimate activity or source. Instead of treating logs as unquestionable truth, organizations need attribution at the session layer.
Activity-aware security verifies the origin of every action. Each keyboard interaction and mouse click is tied to a cryptographically generated hash. Commands are validated in real time against trusted human input. If no verified input exists, the action is rejected immediately.
This changes how SIEM works in practice. Instead of drowning in noisy alerts, security analysts receive events tied to verified activity. That means:
By layering input attribution on top of existing SIEM workflows, defenders turn logs into ground truth. The SOC shifts from reactive analysis to proactive control.
SIEM solution is important for monitoring security events in enterprise environments, but it wasn’t purpose-built to identify who is actually behind the keyboard. This gap is precisely what attackers love to exploit. They can hijack sessions, blend in with normal user activity, and move laterally within a network while SOC teams are busy analyzing logs that show nothing unusual.
Logs can only describe what has happened, but not necessarily who really caused it. To address this issue, it's important to verify input at the session layer. By making SIEM more accurate with intent signals, every command becomes proof that you have a trusted source. Attackers won’t be able to hide their activities behind hijacked sessions, and SOC teams receive alerts they can trust.
Keystrike provides this missing layer. It ensures that every action is validated before it reaches SIEM. The outcome is straightforward: fewer false positives, reduced noise, and an enhanced level of visibility that session hijackers cannot evade.
Try Keystrike in your environment for free for 30 days
