
Ymir Vigfusson
July 23, 2025

Lateral movement turns a minor incident into a major problem. What most teams miss is that it doesn’t necessarily require malware or exploits. Successful breaches exploit trust, which we give to RDP, SSH, Telnet, PowerShell, and WinRM sessions once they’re authenticated.
The protocols themselves aren’t the issue; it’s the assumption that everything inside the session is legitimate.
That’s the assumption Keystrike eliminates. And here’s how you explain it to your team.
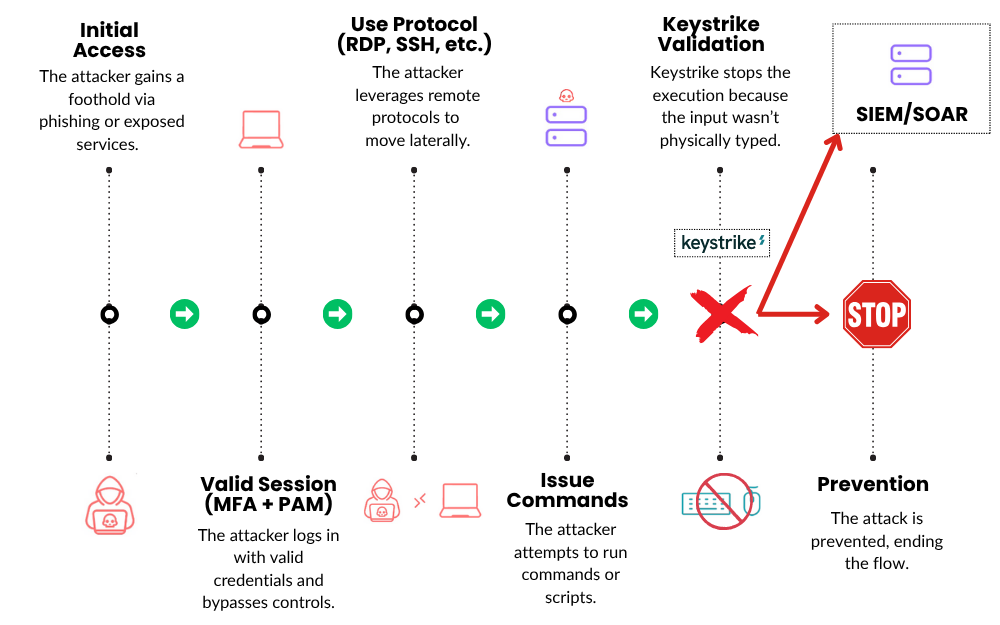
To tackle the problem, we apply MFA, PAM, and a SIEM to help validate identity or log behavior. But none of them ask the most important question at the moment of execution: Was this action initiated by a legitimate, authorized person?
You can authenticate an identity at a point in time, restrict access to a subset of systems, and monitor what happens during a session. But none of that prevents a script from issuing its own commands once a session is active.
The largest attention in cybersecurity tools focuses on defenses around perimeter entry and session visibility. Keystrike shifts the control plane to the point of action, where commands happen. It validates that every command originated from real human input on a trusted device.
Attackers have adapted to use everyday admin tools to move laterally. If you’ve worked an incident, you’ve seen these tools used repeatedly:
Attackers simply reuse trusted channels rather than relying on custom binaries and libraries. All they need is a foothold and credentials, or even just a valid session to reuse. The attack chain continues because the protocols don’t challenge the source of the input.
Let’s walk through each protocol and see what standard tooling sees, and what it misses without attestation.
Scenario: An attacker logs into an exposed IT support machine via reused credentials.
cmd.exe /c whoami && net use \\finance-server\C$If no physical keystroke backs that command, Keystrike blocks the command and signals the intrusion in real time.
Scenario: A script uses stolen SSH keys to exfiltrate data from a production host.
ssh engineer@10.0.0.15 "scp -r /srv/configs/ /tmp/.leak/"Without attestation by Keystrike, the command is dropped at attempted input, because no one typed it.
Scenario: Telnet remains enabled on a network printer or piece of specialized equipment. An attacker scripts a connection to get access.
Keystrike also helps to close legacy gaps without needing to re-architect them, just attest and enforce physical input at the bastion hosts or jump boxes.
Scenario: A malicious session launches an obfuscated PowerShell for recon.
powershell.exe -EncodedCommand SQBtAG...==You need to somehow detect the illegitimate use and signal to your endpoint detection or SIEM/SOAR platform if the real person was not behind the action.
Scenario: Lateral movement using WinRM within a domain-controlled environment.
You need to validate whether remote scripting tools like WinRM are being driven by a real operator or by malware post-compromise. Without that check, your automation surface becomes your blind spot.
You’ve likely deployed these controls:
None of these controls challenge whether the original, authorized human is actually issuing the commands. Once inside a session, the attacker’s commands become indistinguishable from the real user’s. Almost.
You don’t need another alert. You need a control that says: “If my user didn’t type it, take immediate action.”
Keystrike attestation validates that a command came from a trusted input device operated by a real user. No signal? No action. We enforce input-level intent, not behavior-based inference.
You don’t lose sleep because a user clicked a phishing link. You lose sleep because you don’t know what happened after the attacker got in. You’ve locked down accounts, segmented networks, enforced MFA, and tuned your SIEM. But you still ask: What if they’re already inside? What if they’re using my tools against me?
Keystrike is here to solve that question. It doesn't guess and correlate. It enforces the one truth that matters: commands must come from a real human, at a real keyboard, on a trusted device. If that chain breaks, the command never executes.
That’s not visibility. That’s control. You don’t need another alert. You need to end the attacker’s story before it begins. And now, you can.
Try Keystrike in your environment for free for 30 days
