
Keith Casey
November 11, 2025

The U.S. water and wastewater sector is a lifeline service, essential for public health, economic continuity, and emergency response. In 2025, the threat environment continued to intensify. According to the Q1 2025 WaterISAC–EPA National Security Information-Sharing Bulletin, cyber actors are showing heightened interest in operational technology (OT) and industrial control systems (ICS), while physical threats, from drone-borne payloads to insider sabotage, are converging with cyber risks.
Foreign state-sponsored APT groups, such as Salt Typhoon, have demonstrated that sophisticated attack playbooks can be adapted across target sectors. Meanwhile, insecure vendor remote access, exposed ICS interfaces, and under-integrated cyber-physical defenses leave utilities vulnerable.
This article highlights the key trends from WaterISAC’s Q1 2025 bulletin to identify important operational and economic insights and how security challenges impact them.
The water sector’s unique combination of public trust duties and high-availability needs makes it a prime target. Attackers are often driven by potential ransom rewards and also use persistent, targeted disruption for ideological and geopolitical gains.
Today’s utilities are deeply interconnected. OT and IT systems are linked to streamline monitoring, maintenance, and data analytics. This integration improves efficiency but at the cost of broadening the attack surface. A single point of compromise can cascade into operational downtime, safety hazards, or environmental harm.
Physical risks in the water sector compound these challenges. As WaterISAC notes, threat actors, whether state-sponsored, criminal, or extremist, understand the societal ripple effects of success. Even a short outage can erode public confidence and trigger costly emergency responses.
One of the most under-secured pathways into facilities is third-party remote access. Vendors and integrators routinely connect to OT networks for monitoring, maintenance, and upgrades. This means an exposure risk due to:
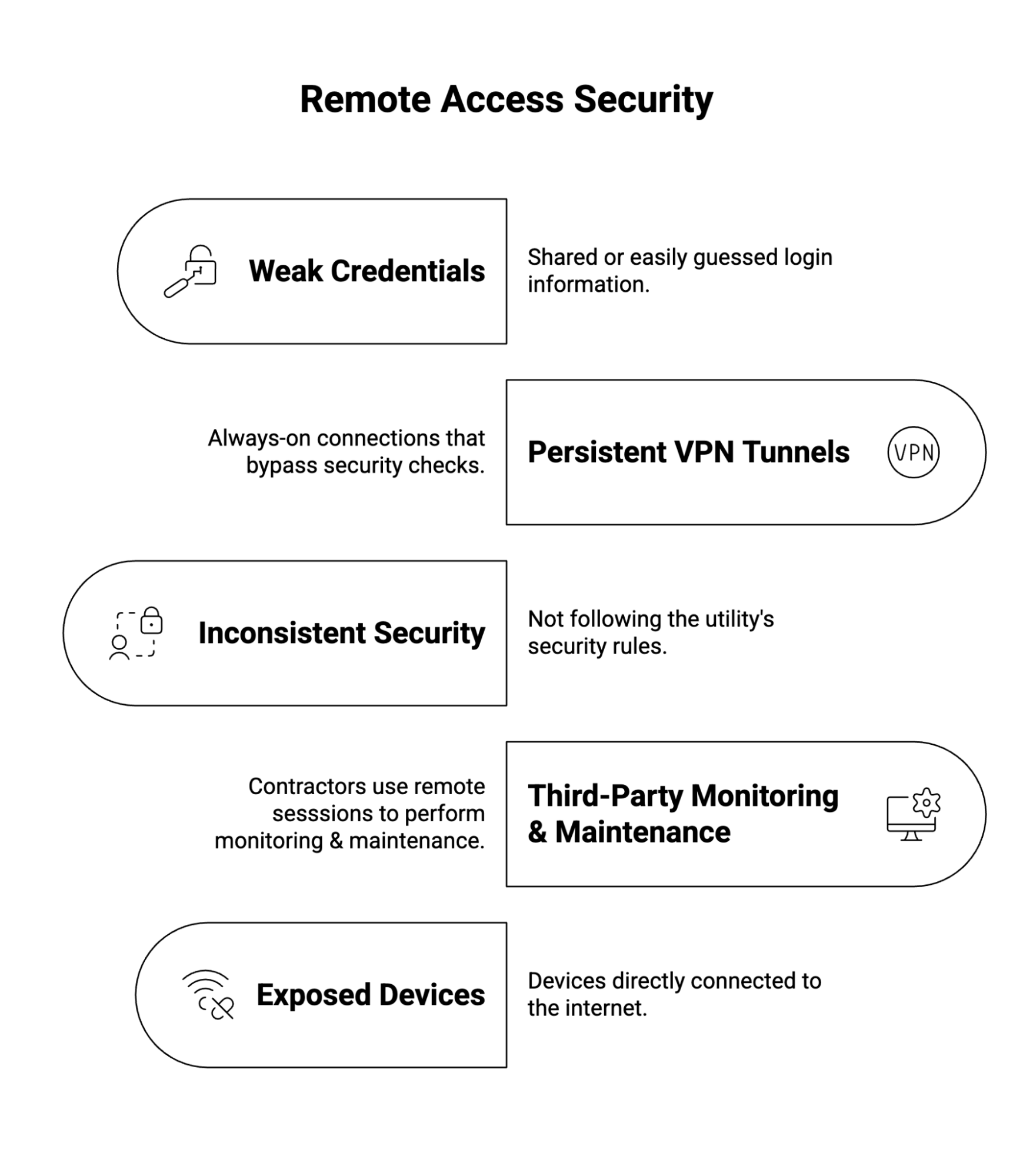
Once inside, an adversary can encrypt critical systems for ransom, move laterally to other assets, or manipulate operational production controls.
Operational Guidance:
For readers in the ICP community, such as CIOs and OT directors, this is a governance issue. If a session cannot be verified as coming from an authorized user at a trusted workstation, it should be denied, regardless of whose credentials are being used. This principle addresses the "lateral movement" opportunity that attackers exploit after initially breaching the environment.
In December 2024, CISA and EPA jointly warned about the dangers of internet-exposed human–machine interfaces (HMIs).
ICS and HMIs are purposefully designed for local operational control, not open internet access. Exposure to outside networks for OT systems could allows attackers to:
Mitigation Priorities for ICS teams and systems:
For technical managers, this needs to be treated with zero-tolerance. Even with seemingly strong passwords, adversaries can brute-force or phish for access.
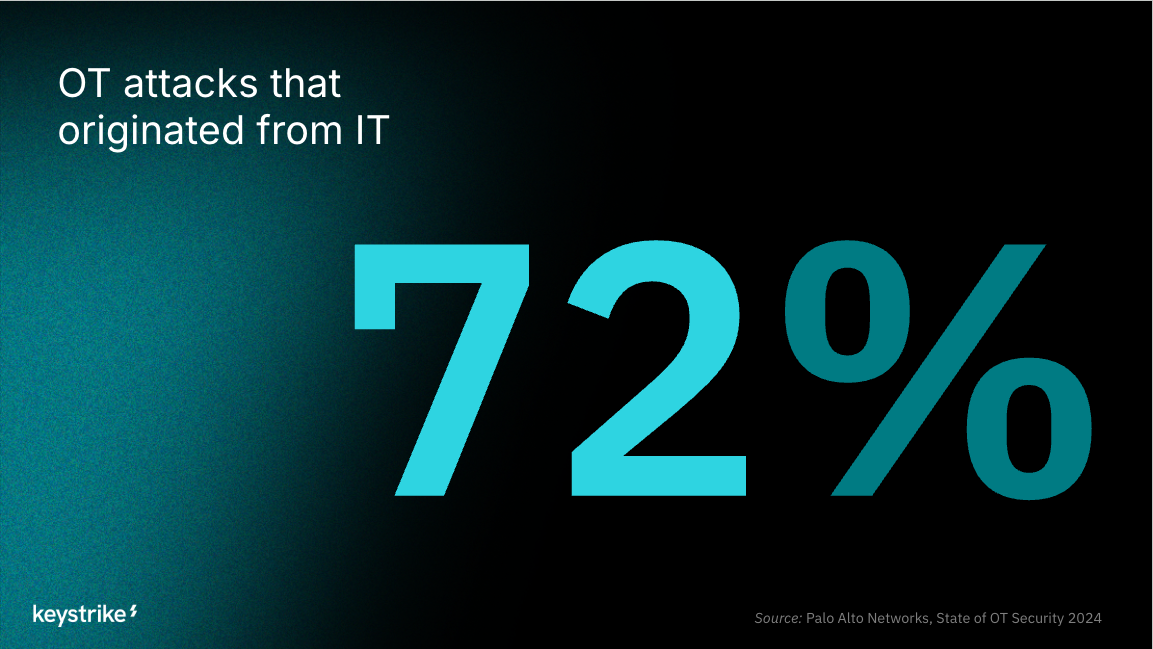
This breach stands as a reminder. Even when attacks target an industry, the techniques and tools used lead to risks for other critical infrastructure sectors. Adversaries adapt proven methods to new targets, and sectors like water and wastewater cannot assume immunity simply because they haven’t yet been named in a campaign.
While the victims were in telecom, the tactics are sector-agnostic:
Why This Matters to Facilities:
Defensive Actions:
Insiders are not limited to payroll staff. Contractors, service providers, auditors, and even janitorial staff may have access to buildings or systems. Risks include:
Common gaps: unlocked access points, open network ports, or unsecured control interfaces.

Practical Measures:
Keystrike-aligned best practice: treat all access, employee, or vendor as “conditionally trusted” until verified in real time.
Drone threats have evolved from nuisance to lethal capability.
Risks to the water sector:
Drones could also facilitate cyber attacks, e.g., dropping wireless sniffers or rogue access points near facilities.
Defensive Priorities:
The National Counterintelligence Strategy’s Goal 7 emphasizes defending water utilities from foreign intelligence entities. Adversaries now blend:
They use advanced tools, AI, drones, and commercial spyware to gather intelligence and disrupt operations.
Implication for Utilities: Counterintelligence is no longer an intelligence agency silo; it’s a utility boardroom topic. Embedding awareness into daily operations, sharing intelligence with WaterISAC, and hardening trust boundaries are now baseline practices.
Drawing from WaterISAC guidance and sector best practices, utilities should:
The Q1 2025 WaterISAC–EPA Bulletin highlights that facilities are facing a threat landscape where the lines between cyber and physical attacks are increasingly blurring. Consequently, trusted relationships with vendors, contractors, and remote sessions have emerged as new high-risk areas.
Protecting this infrastructure demands a mindset shift:
WaterISAC is among the community’s most valuable assets in the battle against escalating cybersecurity risks. We are proud to be involved with the WaterISAC community, which serves as a trusted hub for intelligence, collaboration, and rapid response coordination. The sector’s collective security depends on not just reading their bulletins, but operationalizing them.
The next incident will test readiness. The time to close the remote access integrity gap and lock down critical systems is now.
Try Keystrike in your environment for free for 30 days
